How can I use Okta as an SSO provider for PRTG?
This article applies as of PRTG 22.x.76
Important notice: This article only applies to PRTG Network Monitor, not to PRTG Hosted Monitor.
How to integrate Okta SSO into PRTG
Overview of configuration steps:
- Step 1: Configure Okta
- Step 2: Configure SSO in PRTG
- Step 3: Add a user group in PRTG
Step 1: Configure Okta
Follow these steps to configure Okta to work as an SSO provider in PRTG.
- Optional steps
- Add persons
- Add groups
- Step 1.1: Add an authorization server
- Step 1.2: Create an app integration
Note: Optionally, you can use the API Access Management addon.
Optional steps
Add persons (optional)
Add or import persons who should have access via SSO. For more information, see the Okta documentation: Manage users.
- If you want to add users manually, see the Okta documentation: Add users manually.
- If you want to use a .csv file to import users, see the Okta documentation: Import users from a CSV file.
- After adding the user accounts, make sure to activate them. For more information, see the Okta documentation: Activate user accounts.
Add a group (optional)
You can allow all persons in your Okta to access PRTG, or you can limit the access to a certain group or groups. In that case, use the new group or groups in step 1.1, 1.2, and 3.
Notes:
- By default, Okta creates the Everyone group that includes every person in your Okta. If you do not want to create any groups in Okta, use Everyone as an SSO Group Claim in step 3 (creating a user group in PRTG).
- A user group in PRTG can only have one SSO Group Claim. This means that if you want to use more Okta groups than one, you need to create more user groups in PRTG in step 3, and assign to each one the respective Okta group as the SSO Group Claim.
To create a new group and select its members, follow the steps in the Okta documentation: Manage groups.
Step 1.1: Add an authorization server configuration
For general information about Okta authorization servers, see the Okta documentation: Build Custom Authorization Servers for API Access Management.
- To create a new authorization server, follow the steps in the Okta documentation: Create an authorization server.
Example:
- After saving the new server, add a new claim. Follow the steps in the Okta documentation: Create API access claims.
- In the Add Claim dialogue window, enter the following values:
- Name: Enter groups. Be aware that the name must be in lowercase for the SSO login to work correctly.
- Include in token type: ID Tokens – Always
- Value type: Groups
- Filter: Set a filter that defines which groups will be added to the claim of the token for this authorization server.
If you want to add all available groups to the claim, select Matches regex and enter .*
If you created one or more groups in Okta and you want to limit the claim to these, use the other options, such as Equals, Contains, etc. - Disable claim: Leave unchecked.
- Include in: Any scope
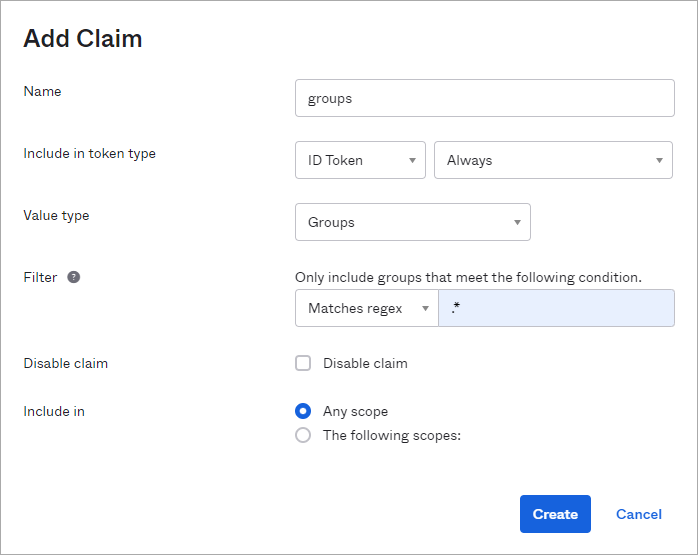
- In the Add Claim dialogue window, enter the following values:
Step 1.2: Create an app integration
For general information about Okta app integrations, see the Okta documentation: Create OpenID Connect app integrations.
- In the Create App Integration dialogue window, select the following settings:
- Sign-in method: OIDC – OpenID Connect
- Application type: Web Application
- In the New Web App Integration dialogue window, enter the following:
- Enter an App integration name.
- In Grant type, select Authorization Code and Refresh Token.
- In Sign-in redirect URIs, enter the IP addresses or DNS names of the PRTG installation(s) that your users use to access PRTG. Use the format https://<IP address or DNS name>:port/cb.
Example: https://myprtg.domain.com:443/cb.
Note: You can skip this step for now and add the URLs when you configure SSO in PRTG. - In Controlled access, select Allow everyone in your organization to access.
If you selected Limit access to selected groups, enter the name(s) of the group(s) that you want to grant access.
Step 2: Configure SSO in PRTG
Now that you have configured Okta, proceed to configure the SSO settings in PRTG.
- Log in to the PRTG web interface.
- Go to Setup | System Administration | Single Sign-On.
- In SSO Login, select Enable.
- In Provider, select Okta.
- In Configuration Endpoint, enter the configuration endpoint URL as follows https://<yourOktaDomain>/oauth2/<authorizationServerId>/.well-known/oauth-authorization-server
Note: This is the Metadata URI endpoint that you can find in the Okta administrator console in Security | API | <Your Authorization Server>. - Click Load Configuration. This automatically fills in the values in the next four fields.
Note: If this does not work, enter the values manually as follows. Use your Okta domain and your authorization server ID.- Authorization Endpoint: https://<yourOktaDomain>/oauth2/<authorizationServerId>/v1/authorize
- Token Endpoint: https://<yourOktaDomain>/oauth2/<authorizationServerId>/v1/token
- JSON Web Key Set (JWKS) URI: https://<yourOktaDomain>/oauth2/<authorizationServerId>/v1/keys
- Issuer: https://<yourOktaDomain>/oauth2/<authorizationServerId>
- In Scope, enter openid offline_access email profile. The required scopes are added by default after you add your authorization server. You can find the scopes of your authorization server in the Okta administrator console in Security | API | <Your Authorization Server>.
- In Application (Client) ID, enter the Client ID that you can find in the Okta administrator console in Applications | Applications | <Your Application>.
- Under Client Secret, enter the client secret that you can also find in Applications | Applications | <Your Application>.
- In Available Callback URLs, select the URLs that your users will use to log in to PRTG.
Example: https://myprtg.domain.com:443/cb.
If you haven't done so in Step 1.2, add these URLs to your application in the Okta administrator console. Go to Applications | Applications | <Your Application> and fill the Sign-in redirect URIs field. After that, return to the PRTG web interface and continue with the following steps. - If the URL your users use to log in to PRTG is not listed because PRTG is reachable via a different URL (for example, myPRTG.example.com for login but PRTG lists myPRTG.internal.example.com), you can use the option Manually enter a URL. PRTG still lists all available endpoints if needed for forwarding. You must also add these URLs to your application in the Okta administrator console. Go to Applications | Applications | <Your Application> and fill the Sign-in redirect URIs field
Note: Both Okta and PRTG check if the callback URLs are allowed. Make sure you configure each required URL on both ends; otherwise, the users will not be able to log in. - Click Test Single Sign-On Authorization Endpoint and wait for the success message.
Note: To test the SSO successfully, you must open your PRTG installation via a URL that you have configured as a valid redirection URI in the Okta administrator console.
- Click Save.
You have now configured SSO in PRTG.
Step 3: Add a user group in PRTG
Now that you have configured SSO, add a new user group in PRTG.
- Log in to the PRTG web interface.
- Go to Setup | System Administration | User Groups.
- Hover over the blue (+) button and select Add User Group.
- In User Group Name, enter a name to identify the group, for example, Okta SSO User Group.
- In Active Directory or Single Sign-On Integration, select Use single sign-on integration.
- In SSO Group Claim, enter the access claim for the SSO group. This is the name of the Okta group for whose members you want to grant access to PRTG. If you want to grant access to all persons in your Okta, enter Everyone.

- Click Create.
You have now successfully integrated Okta as an SSO provider in PRTG.
Note: PRTG creates local user accounts of SSO users only after they have successfully logged in PRTG.
